
- Home
- Technology
- Smoke, Mirrors, and Breaches: What’s...
Smoke, Mirrors, and Breaches: What’s Really Happening in India’s Cyber Space
From data leaks and ransomware to underreported breaches, India’s digital infrastructure remains vulnerable, and regulatory enforcement is struggling to catch up.

As tensions flared across the India-Pakistan border in early May following a deadly terror strike in Jammu and Kashmir, another front opened up — not in the air or on land, but across servers and screens.
A series of Distributed Denial-of-Service (DDoS) attacks flooded Indian websites with fake traffic, temporarily knocking several government portals and financial platforms offline. (DDoS attacks overwhelm a website with excessive data requests, rendering it inaccessible to real users.)
In a matter of days, Telegram and dark web channels were abuzz with claims from multiple Pakistan-linked hacktivist groups. Lists of supposedly defaced Indian websites were circulated widely, with warnings of further breaches targeting everything from stock exchanges to Aadhaar-linked databases.
On May 11, cybersecurity firm CloudSEK reported over 100 claimed cyberattacks attributed to Pakistan-backed groups in just the first two weeks of the same month.
But when researchers dug deeper, most of those claims didn’t hold up.
“Any experienced downtime appears to have been negligible, potentially lasting less than five minutes, suggesting the attacks had no significant or sustained impact on the availability of these critical government services,” CloudSEK said in its latest threat intelligence
As tensions flared across the India-Pakistan border in early May following a deadly terror strike in Jammu and Kashmir, another front opened up — not in the air or on land, but across servers and screens.
A series of Distributed Denial-of-Service (DDoS) attacks flooded Indian websites with fake traffic, temporarily knocking several government portals and financial platforms offline. (DDoS attacks overwhelm a website with excessive data requests, rendering it inaccessible to real users.)
In a matter of days, Telegram and dark web channels were abuzz with claims from multiple Pakistan-linked hacktivist groups. Lists of supposedly defaced Indian websites were circulated widely, with warnings of further breaches targeting everything from stock exchanges to Aadhaar-linked databases.
On May 11, cybersecurity firm CloudSEK reported over 100 claimed cyberattacks attributed to Pakistan-backed groups in just the first two weeks of the same month.
But when researchers dug deeper, most of those claims didn’t hold up.
“Any experienced downtime appears to have been negligible, potentially lasting less than five minutes, suggesting the attacks had no significant or sustained impact on the availability of these critical government services,” CloudSEK said in its latest threat intelligence report.
While the India Computer Emergency Response Team (CERT-In) logged over 1.39 million cybersecurity incidents in 2022 (the most recent data available) — ranging from phishing, malware, ransomware, to identity theft — the recent wave of cyber chaos was more about perception than precision.
CloudSEK and other threat intelligence firms noted that some websites listed as “defaced” by Pakistan-linked groups were either still functioning normally or not hosted in India at all.
The attacks seemed less about disruption and more about optics — a symbolic digital war waged for maximum narrative control.
Although cyber warfare continues unabated, with Indian hacktivist groups themselves launching retaliatory cyberattacks against Pakistani websites and government services, it raises a crucial question: How prepared are India's private and public enterprises, tech startups, and critical government infrastructure to handle sustained and serious cyberattacks?
Not very well, according to recent data and expert analyses.
Cyber Lapses Are National Security Risks
A Cisco Cybersecurity Readiness Index (2022) found that only 24% of Indian companies operate at a mature stage of cyber preparedness, while more than 30% remain stuck at the "beginner" level, severely lacking in even foundational security protocols. This translates into an alarming number of firms without robust continuous threat monitoring, incident response plans, or basic protective measures.
“Most people don’t invest in proper security measures; they think it’s too much of an expense. At best, they’ll invest in a good firewall and that’s it,” Rajgopal AS, managing director and CEO of NxtGen, told The Core.
“Serious customers spend 15% of infrastructure cost on security, but most don’t even spend 5%. And when companies do get breached, they usually don't report it…these incidents don't come out until it’s picked up on the dark web or publicly leaked.”
The recent conflicts have exposed how fragile critical infrastructure can become during periods of geopolitical strain.
According to CERT-In, reported cyber incidents in the country jumped from roughly 3.94 lakh in 2019 to 11.6 lakh in 2020, and further to around 14 lakh in 2021.
The latest India Cyber Threat Report 2025, jointly published by the Data Security Council of India (DSCI) and Seqrite, paints an even grimmer picture.
The detection of over 36.9 crore security incidents across 84.4 lakh endpoints in a single year translates into an average of 702 potential security threats every minute. That’s roughly 11 new cyber threats every second somewhere in the country.
“This volume of attacks demonstrates the relentless nature of modern cyber threats and the constant pressure on security systems,” the report had noted.
Amid the noise of symbolic attacks like website defacements and short-lived DDoS attacks, cybersecurity researchers caution that the real danger comes from sophisticated cyber-espionage groups, known as Advanced Persistent Threats (APTs).
During the attacks in May, threat intelligence reports specifically pointed to increased activity by APT36 (Transparent Tribe), a notorious Pakistan-based hacker group known for targeting Indian defence installations, government entities, and educational institutions.
According to cybersecurity firm CloudSEK, within 48 hours of the April 22 terror attack in Pahalgam, APT36 leveraged emotionally charged phishing emails disguised as official government documents, tricking users into downloading a malicious payload called Crimson RAT, capable of infiltrating sensitive Indian defence and government networks.
“Now the cyber attacks (during wartime situations) are not just monetary-linked but are more of a name and shame game as well. But deeper down, APTs are the real threat. These groups have the time, resources, and intent to quietly infiltrate sensitive systems and remain undetected for long periods,” Arati Hiremath, Vice President – Asia Pacific at CGI, told The Core.
Rajgopal of NxtGen also pointed out that volumetric attacks, such as DDoS attacks and website defacements, can just be distractions. The real concern is organised groups like APTs who can enter private companies and even government networks silently, remain hidden for months, and extract critical data before anyone even notices.
Historically, India has faced multiple intrusions by state-backed APT groups. Notable examples include the RedEcho attack in 2021, attributed to China-based hackers, targeting India’s power grid amidst border tensions.
Another alarming incident involved the 2019 infiltration at the Kudankulam Nuclear Power Plant, linked to North Korea’s Lazarus Group, marking one of the first public instances of cyber threats penetrating critical nuclear infrastructure in India.
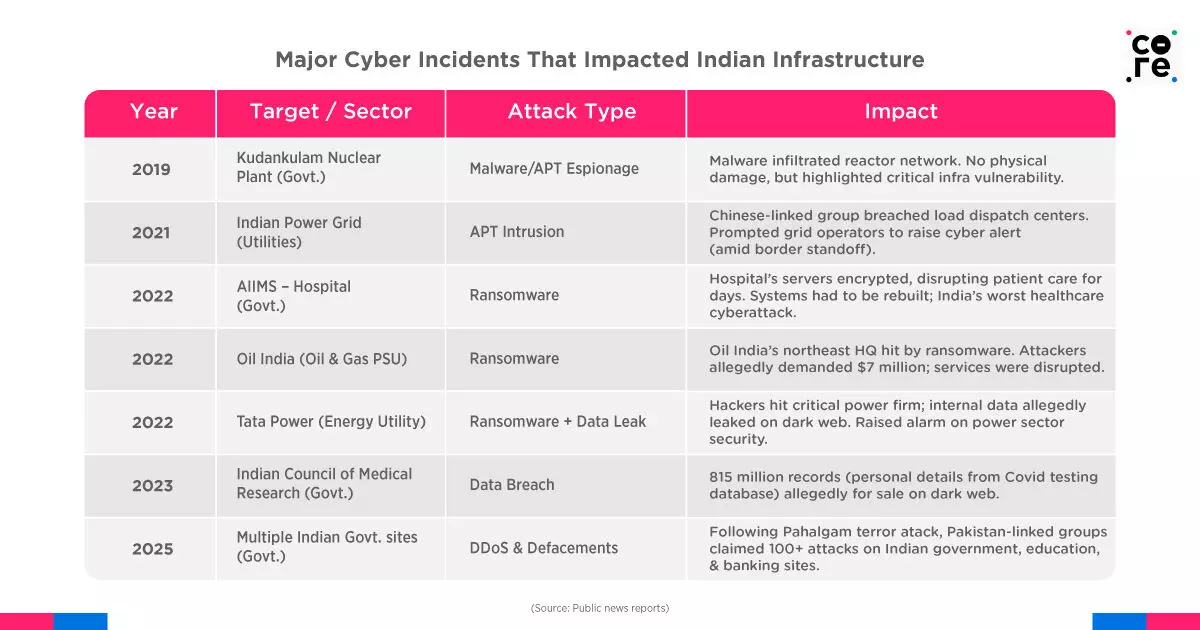
Given this backdrop, cybersecurity preparedness isn’t merely a compliance issue — it’s a national security imperative. Yet Indian MNCs, tech startups, small and medium enterprises (SMEs), government agencies, and even core sectors (healthcare, energy, banking, etc) still lag significantly in robust cyber defences.
As the examples above in the table clearly show, Indian entities face a wide array of cyber threats. Yet, the risk that stands out most vividly is that of data breaches and leaks, driven predominantly by black hat hackers (individuals who exploit cybersecurity weaknesses maliciously for personal gain). These cybercriminals relentlessly scour the software infrastructure of tech companies, startups, and MNCs, looking for security gaps to exploit and breach sensitive databases.
Most Indian Firms Remain Soft Targets
In recent years, India has suffered multiple high-profile data breaches, compromising hundreds of millions of personal and financial records.
The Aadhaar system, with biometric data of over 1.3 billion Indians, witnessed breaches like the Indane gas leak exposing 6.7 million Aadhaar numbers (2019), and the massive 2023 leak involving personal records of 81.5 crore individuals allegedly tied to Aadhaar and COVID-19 testing data.
Similar breaches have exposed millions more in the private sector as well: BigBasket’s 20 million user records (2020), Domino’s 180 million order records (2021), MobiKwik’s 8.2TB data leak affecting 100 million users (2021), and several others.
These numbers show that despite increasing awareness, vast segments of Indian businesses remain exposed.
“Security is seen as a cost until a breach happens, but prevention is always cheaper than damage control,” Ruchin Kumar, Vice President – South Asia at Futurex, told The Core.
“Startups and other tech firms often invest in cybersecurity only after facing regulatory audits or public breaches — not proactively.”
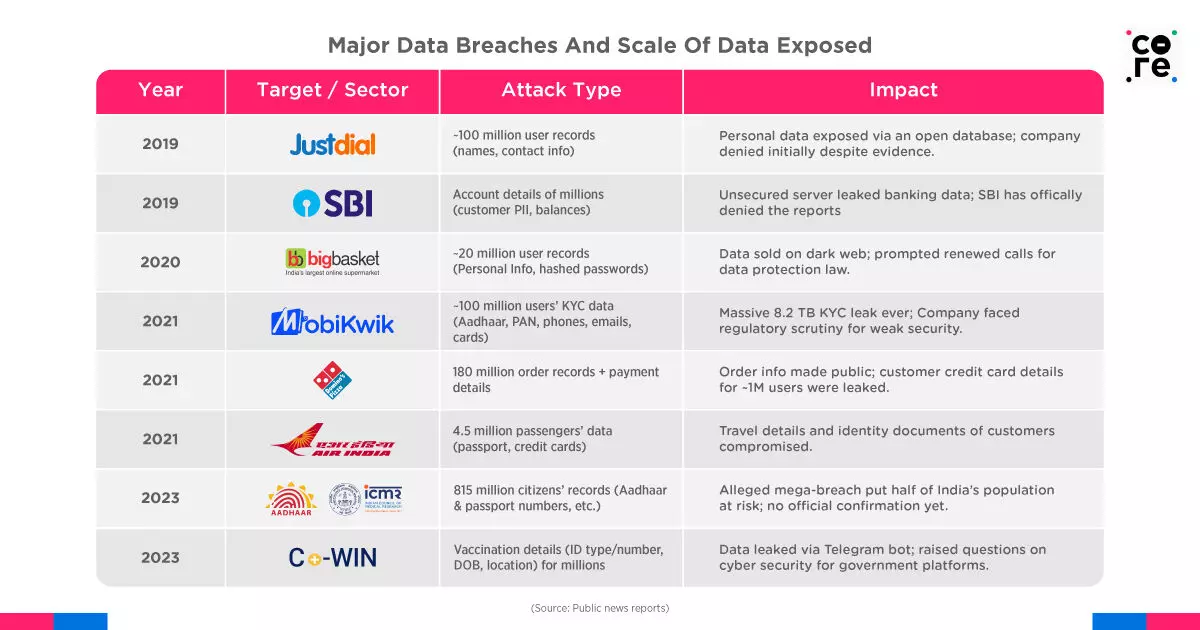
When vast troves of customer, client, and employee data — including emails, passwords, phone numbers, physical addresses, and financial details — fall into the hands of hackers, it fuels an ecosystem ripe for fraud, phishing scams, identity theft, and privacy violations.
And in times of heightened geopolitical tensions, such leaked personal data can become a powerful weapon, enabling malicious actors and state-backed cybercriminals to precisely target civilians, sow confusion, and exploit vulnerabilities.
The Disclosure Deficit
Despite the frequency and severity of attacks, many Indian companies still choose to stay silent about breaches — often in violation of existing laws. According to experts, fear of reputational damage, legal scrutiny, and unclear enforcement mechanisms have created a culture of denial and delay.
“Most companies get breached, but they don’t report. They wait until it’s picked up on the dark web or publicly leaked,” Rajgopal of NxtGen, told The Core.
Sonam Chandwani, managing partner at KS Legal & Associates, confirmed this pattern, pointing out that breach disclosures usually come not from companies, but from media reports or independent cybersecurity researchers.
“This reluctance to report breaches stems from concerns over reputational damage, financial losses, and weak regulatory enforcement, which diminishes the incentive for transparency,” Chandwani said.
“CERT-In provides guidance and coordination for incident response, but its advisory role is limited by a lack of enforcement authority and resources.”
Even large firms are often reactive rather than proactive. Arati Hiremath, Vice President — Asia Pacific at CGI, noted that many organisations wait for a crisis before hardening their defences.
“I think it's time for us to change the way we look at things,” Hiremath told The Core. “Security isn’t just about incident management—it’s about building a culture of resilience long before something breaks.”
The Regulatory Vacuum
India does have a cybersecurity reporting framework in place—at least on paper. The CERT-In directives issued in 2022 require companies to report cyber incidents such as data breaches, ransomware attacks, or unauthorised access within six hours.
However, that timeline is widely considered impractical, especially for small and mid-sized organisations that may not even detect the breach within that window.
In parallel, the much-anticipated Digital Personal Data Protection (DPDP) Act, 2023, is expected to bring stricter compliance requirements, including mandatory breach notifications to a newly formed Data Protection Board (DPB).
Penalties for non-compliance could go as high as Rs 250 crore. But until clear rules are published and the DPB becomes fully operational, most companies are left in regulatory limbo.
Moreover, India still lacks a dedicated and centralised cybersecurity regulator, akin to the General Data Protection Regulation (GDPR) in Europe or CISA in the United States. In the absence of such a body, CERT-In plays a limited role, issuing advisories and threat alerts—but without the teeth to enforce compliance or investigate lapses.
While existing frameworks do allow for enforcement, penalties have been sporadic at best. Notable examples as pointed by Chandwani of KS Legal include the 2020 penalty imposed on HDFC Bank under Section 43A of the IT Act for inadequate security measures that led to a data breach, and Union Bank, which faced a Rs 1 million fine from the Reserve Bank of India (RBI) for failing to comply with cybersecurity guidelines.
Sectoral regulators like the RBI and the Securities and Exchange Board of India (SEBI) have shown they can act, but enforcement has remained inconsistent. CERT-In, for its part, lacks prosecutorial powers and focuses largely on issuing advisories.
Without routine audits and real-time oversight, these regulatory gaps have allowed many vulnerabilities to persist unchecked.
From data leaks and ransomware to underreported breaches, India’s digital infrastructure remains vulnerable, and regulatory enforcement is struggling to catch up.

